The Threat Inside: Why Middle East Leaders are Adopting a Zero Trust Mindset with AI
Tech leader Sandeep Mundra explains the shift in the Middle East towards AI-driven Zero Trust security to combat insider threats, highlighting the critical role of behavior analytics and strategic partners like NICGulf in safeguarding corporate data in a rapidly digitizing landscape.

Your Biggest Security Risk Isn't Outside the Walls-It's Already Inside
For a quarter of a century, I've sat in boardrooms around the world, from fledgling startups in Bangalore to established enterprises in London. The conversation about cybersecurity, for the longest time, was always about building a bigger wall. A stronger firewall, a more complex antivirus, a taller digital fortress to keep the bad guys out. Yet, time and again, I've seen the most sophisticated defenses fall not from a frontal assault, but from a single key turned on the inside. The most damaging threats often don't break down the door; they walk right through it with legitimate credentials.
This is the uncomfortable truth of the insider threat. And in a region undergoing one of the most rapid digital transformations in human history-the Middle East-this truth is becoming a critical business priority. As companies in hubs like Dubai's Business Bay digitize their operations and embrace the cloud, their most valuable asset, data, becomes both more accessible and more vulnerable. The old model of perimeter security is obsolete. The new imperative, which we'll see dominate the security landscape by 2026, is identity. It's about securing your data from the inside out.
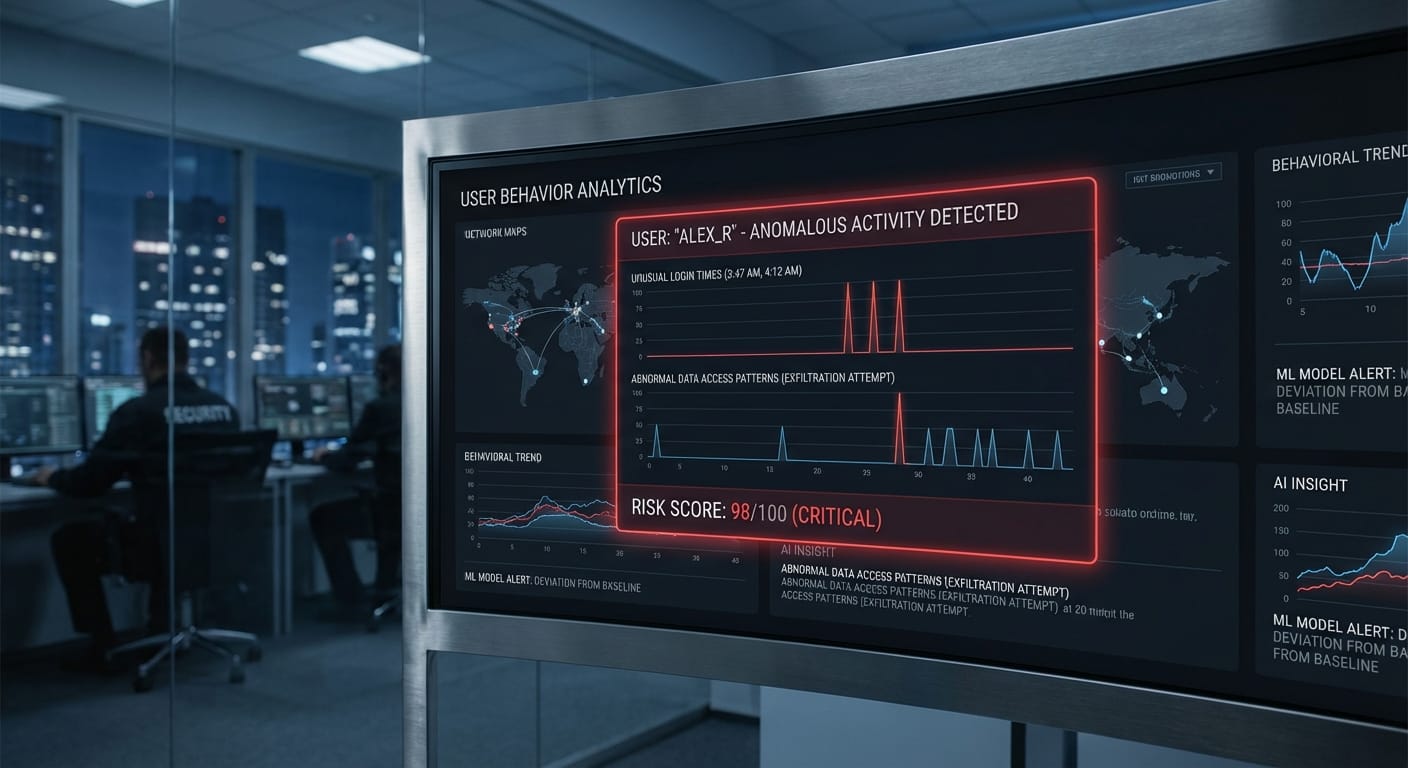
The focus is shifting from preventing breaches at the border to detecting malicious activity within the network. And the only way to do that at scale and with precision is with Artificial Intelligence.
The New Battleground: Why Identity Security is the 2026 Priority
The economic dynamism of the UAE and the broader Middle East is built on trust, innovation, and speed. However, this very environment creates a perfect storm for insider threats. These threats are not always born of malice; they often stem from negligence or compromised credentials where an employee's account is hijacked by an external actor. Regardless of intent, the result is the same: unauthorized access to sensitive corporate data.
A Story of a Lesson Learned the Hard Way
I remember a client from about fifteen years ago, a fast-growing financial services firm. They had state-of-the-art perimeter security. One day, their entire customer database appeared for sale on the dark web. There was no sign of a breach, no alarms triggered. After weeks of frantic investigation, they discovered the source: a departing systems administrator had quietly copied the data to a personal drive a month before his resignation. He wasn't a master hacker; he was just an employee with excessive permissions and a grudge. Back then, our tools were primitive. We had logs to sift through manually, a digital needle in a haystack. Today, AI-led behavior analytics would have flagged his anomalous data access in real-time, turning a company-crippling disaster into a manageable security alert.
The perimeter is dead. Security is no longer a line you draw around your company, but a principle you apply to every single user, device, and data request, every single time. This is the essence of Zero Trust.
Organizations are realizing that their defenses must be as dynamic as their workforce. The rise of remote work, cloud applications, and complex supply chains means the "inside" of a company is no longer a physical office but a fluid network of identities.
Fighting Fire with Intelligence: AI-led Behavior Analytics and Zero Trust
So, how do you catch a threat that looks like a legitimate user? You stop looking at static rules and start analyzing dynamic behavior. This is where the powerful combination of a Zero Trust framework and AI-driven analytics comes into play. It's a fundamental shift from a reactive to a proactive security posture.
The Pillars of a Modern Defense Strategy
A Zero Trust architecture operates on a simple but powerful principle: never trust, always verify. It assumes that no user or device is inherently trustworthy, whether inside or outside the network. To implement this effectively, you need intelligence, which AI provides through User and Entity Behavior Analytics (UEBA).
- Establishing Baselines: AI algorithms first learn the normal patterns of behavior for every user and device. What time does an employee usually log in? What data do they typically access? From where do they connect?
- Detecting Anomalies: The system then monitors for deviations from this baseline in real-time. An accountant suddenly trying to access source code at 3 AM from an unrecognized location is a major red flag that a rules-based system might miss.
- Automating Response: When a high-risk anomaly is detected, the system can automatically trigger a response, such as requiring multi-factor authentication, restricting access, or alerting a security team for immediate investigation.
- Reducing Alert Fatigue: Unlike older systems that generate thousands of false positives, AI is smart enough to differentiate between a benign anomaly (like logging in while traveling) and a genuinely suspicious one, allowing security teams to focus on real threats.
The table below highlights the stark difference between these approaches. Based on industry analysis, the advantages are not just incremental; they are game-changing.
| Security Model Feature | Traditional Perimeter Security | AI-Driven Zero Trust Framework |
|---|---|---|
| Core Principle | Trust but verify (Trust internal users by default) | Never trust, always verify (Explicit verification required) |
| Threat Detection Method | Signature-based (Catches known malware/attacks) | Behavior-based (Identifies anomalous activity) |
| Avg. Insider Threat Dwell Time | Over 7 months (Ponemon Institute Data) | Minutes to hours |
| Primary Focus | Protecting the Network Edge | Protecting Data and Resources |
NICGulf: Your Partner in Building a Resilient Enterprise
Implementing a Zero Trust framework isn't about buying a single product; it's about adopting a new security philosophy and having a strategic partner to guide you. For companies in Business Bay and across the UAE, NICGulf is that partner. They understand that security must enable business, not hinder it. Their approach is pragmatic and tailored to the unique risks and regulatory environments of the region.
Here is how they help organizations make the critical shift to a modern security posture:
- Strategic Assessment & Roadmap: NICGulf begins by analyzing your current security posture, identifying critical data assets, and mapping user access patterns to build a phased, achievable roadmap to Zero Trust.
- Identity-Centric Control Implementation: They deploy robust Identity and Access Management (IAM) solutions, ensuring the right people have the right access to the right resources, and nothing more.
- AI-Powered Threat Detection Deployment: By integrating advanced behavior analytics platforms, they provide real-time visibility into your network, enabling the instant detection of suspicious activities that signal an insider threat.
- Continuous Monitoring and Optimization: Security is not a one-time project. NICGulf provides ongoing support to fine-tune the system, respond to incidents, and adapt your defenses as new threats emerge.
Conclusion: The Leadership Decision for 2026 and Beyond
As leaders, our responsibility is to protect our organizations from foreseeable risks. For years, we focused on the enemy outside. Now, the data is undeniable: the most persistent and damaging threats are already within our systems. Continuing to rely on perimeter security alone is like locking the front door while leaving all the internal doors wide open.
The move toward a Zero Trust architecture, powered by AI, is not just a technical upgrade; it is a fundamental business decision. It is an investment in resilience, trust, and the long-term integrity of your enterprise. The question is no longer *if* you should adopt this model, but *how quickly* you can. If you are ready to secure your organization from the inside out and build a truly resilient enterprise, I encourage you to speak with the experts at NICGulf. The future of your business may depend on it.




